Important elements of the analysis:
Compiled on 29th December 2024
PowerShell multi-stage infection dropping
Remote Access Trojan
External devices infection spreading
Administration rights required for execution
Abuse of Github repository to drop of XClient artifact
Windows Defender evasion
Installed Antivirus products obtaining
Attempt of fileless approach with malicious second-stage malware artifact named RuntimeBroker.exe
Infostealer
Keylogging
DDos attacks launch in the capabilities
SecureString objects used to deal with stolen credentials
Screen logging and capturing
C&C communications and Xchat sockets connections encrypted
AES encryption used
Uninstaller script to remove the threat
RDP service of the C&C IP address
DNS poisoning via editing of Hosts file
Ping connections to the C&C IP address
In the present article I analyze an XWorm threat compiled on 29th December 2024, it is developed in .NET with calls to PowerShell process of artifacts dropping. XWorm is a Remote Access Trojan that can be customized in a Malware-as-a-Service approach and finally sold in the dark market. The threat can steal sensitive data, perform cryptowallets stealing, perform ransomware attacks, malicious remote access and it is spread mainly with phishing, spearphishing malicious emails and external devices infections.
MITRE matrix:
Here below we can see evidences related to administrator rights for the execution flow, execution of the PowerShell commands. It is curious to notice the fact there are comments associated to what is done in the programming flow that calls the Github page of the repository used for the XClient.exe execution github[.]com/rosarioian181/meeekone/. The PowerShell commands also permit to perform the downloading of the infection stages payloads, exclusions on Windows Defender to avoid detection and blocking with the cmdlet “Add-MpPreference -ExclusionPath”
The artifact drops a fake RuntimeBroker.exe executable under $env:Temp folder which is the second stage payload, after the download phase it begins the executions phase.
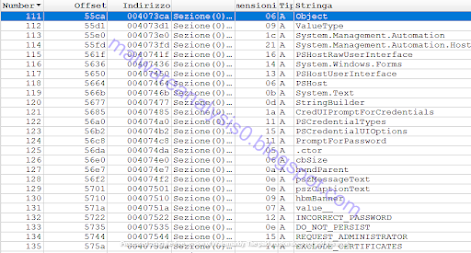
There are references to items related to credentials and login information, such as Credential_Form, CREDUI_INFO, CREDUI_FLAGS, CredUI_ReturnCodes, User_PwD, interface elements related to keyboard handling process, such as Keyboard_Form.
The XWorm uses the class System.Management.Automation.PSCredential to manage captured credentials, usernames and passwords, login details. We can see the error use case “INCORRECT_PASSWORD”.
Following are the certificates details related to certificate options, smartcard requirement option, server credentials and the domain information.
Here we have details related to keystrokes recording and logging, event handlers, such as GetCharFromKeys to convert key codes to chars, the event handlers for the buttons pressing KeyDown and KeyUp in the managed form.
Following are files types and I/O operations constants, which represent file types, std I/O.
Here are references to credentials, login details and maximum size:
Here are others references to keystrokes logging, key event handlers. PSRunspace-Host is included in the PS2EXE tool which performs actions of conversion of PowerShell scripts to executable files. The module in question is related to the phase of the prepare of the script Customer.ps1, which is also used and launched in executable file type.
The XWorm threat requires high privileges to run as Administrator:
Here are some hexadecimal code details which contain exceptions handling and the details of the entropy status of the artifact:
The entropy of the first stage artifact is not so high and the .text section is not packed:
Here we have the details associated to the credential form with credentials information in input. The user password is created with a specific object type with the class User_Pwd and created a new instance, the credential information are created with StringBuilder objects.
A PowerShell process instance is used to execute a while loop with the reading operation with the Console.ReadLine() method to obtain the data inserted got in the “text2” variable with a PSDataCollection object.
Here we have details related to the foreach loop which analyzes the arguments parameters used in the PowerShell commands executed and with particular attention to -wait, -extract, -end, -detailed and -debug options for the PowerShell converting phase.
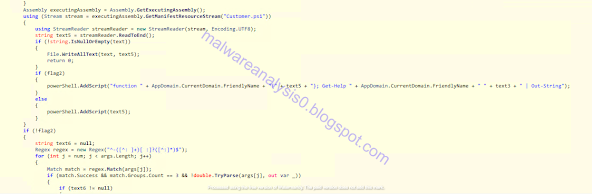
An Assembly object is created to get the resource stream of the launched script of dropping Customer.ps1. To the script also the AppDomain is added. In the if construct, after the "flag2" check, there are appended function script methods and Out-String to get the output of the script in the stream reader in string type, otherwise the read stream (contained in the "text5" variable) is added in the "powerShell" variable
Some parameters of the PowerShell scripts are checked against boolean values and depending on that others parameters are added.
The output type of the PowerShell commands is string (Out-String):
The method getPassword is of type SecureString to prevent data obtaining through memory dump, when Enter key is pressed a break is reached in the while (true) loop, that means the password has been inserted, if the lenght of the password is greater than zero two backspace characters are added to the last position, if the keycode of the pressed button is different from zero, in the console an asterisk symbol is written.
The method of type PSCredential PromptForCredential takes the inserted password and, if different from null, the characters are added to a character array.
A Dictionary method called Prompt of types string and PSObject is used to add details such as captions and assembly information in the dropped artifact. When the second stage payload is dropped, .NET compiling .cmdline temp files are created, this is related to a runtime compile operation.
A try-catch construct is then used and the inserted type is checked against PSCredential and SecureString types, if they are different from those types of objects the ib_message attributes are filled in:
If the symbols “!?” are inserted in phase an help message is displayed.
Here we have the construction of the PSCredential object pSCredential which starts with four empty strings, then the attributes are filled in with SecureString type, finally the dictionary variable is returned.
Here are the keyboard events handlers, developed in particular for such particular cases of special keys, such as “Shift”, “Alt”, “Ctrl”, “CapsLock”, etc.
The static method GetCharFromKeys of type string converts the keys pressed to characters:
We have details associated to keyboards form and GUI elements related to keys event handlers:
From a first OSINT overview we can see the IP Address 147.124.210[.]158 is related to the XWorm threat, as we will see later this will be an interesting indicator for infostealing and remote access C&C.
With a dynamic analysis approach we can see the PowerShell commands of the first stage artifact to perform Windows Defender exclusions.
Here we have the downloading on the XClient artifact from Github repository abused: github[.]com/rosarioian181/meeekone.
The second stage artifact downloaded through the first stage payload from the abused Github repository is XClient.exe and then the executable RuntimeBroker.exe is dropped in C:\Users\<USER>\AppData\Local\Temp:
The second stage dropped Portable Executable is developed in VB .NET, its hash is e328af9decf08bcaab7ada74100cc56186383a3bf51c9de6a9d7b41ea3aea094 and it has been compiled on 21st December 2024:
Here we have some extracted strings from the PE, there are references to ClientSocket objects, Settings for the XClient, Messages of the sockets communications for the executed commands, Uninstaller tool. The Uninstaller tool is used to remove the XWorm artifacts and its traces.
The artifact obtains details related to the infected host, system details and user information to individualize the victim.
A mutex attribute is used in the ComputeHash function in the Decrypt method in the AlgorithmAES class for the Helper.SB object. There are references to isConnected boolean values for the socket connections instances.
The XClient artifact manages the communication to the C&C server via socket instance, the details contained in the enumerations of the XWorm infection are encrypted with AES algorithm.
The infection methods related to socket and C&C connections and communications are hidden from the debugger.
Some attributes are in part encoded in Base64, there are functions to shutdown socket connections:
The artifact gets registry data and details to perform the infection cycle and infected host information (like get_CurrentUser) and settings.
The strings CopyFromScreen and get_Jpeg indicate us one interesting aspect of XWorm: the stealing of screen captures.
Here we have HttpWebResponse and HttpWebRequest functions, that are used in C&C communications phases. A different useragent is set to avoid simple detection of an automated malicious connection. The WriteAllBytes function is used in the context of writing data in socket communications.
Following are references to encryption subroutines used: RijndaelManaged, SymmetricAlgorithm, ICryptoTransform and hashing functions (MD5CryptoServiceProvider).
Here we have the lunch arguments of the XClient PE, with the encrypted and encoded attributes:
Some WMI queries are used to gather information about installed antivirus products, GUI information, shutdown commands to restart the machine and then we have the StartDDos and StopDDos functions that could be used to perform crafted DDos attempts.
The Xchat is used to perform messages in the remote access phase, the hosts file is modified to perform DNS poisoning attacks. An offline keylogger version is not enabled in the malicious package by default.
Here we have the details of strings associated to DDos function and POST requests details (also used in TD method), useragent details changing (such as iPhone, Windows 64 Bit), content-lenght of the HTTP packet.
Here are the attributes encrypted hardcoded in the XClient artifact, the KEY attribute is the AES Encryption key.
Here we have the AlgorithmAES class which contains the Decrypt method with RijndaelManaged and MD5 algorithms objects.
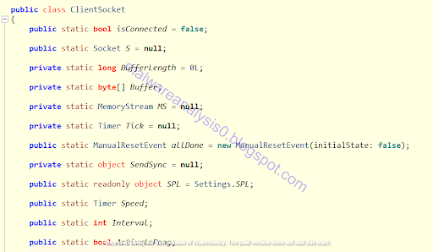
The ClientSocket class contains the most important attributes and functions related to the C&C communications, ping and “pong” events, buffers of data used, memory stream objects and data sending events.
The BeginConnect used the Settings.Hosts attribute to start the C&C communications and it is split with a comma symbol.
The static method ConnectServer of object type perform server connections to receive data buffers, the SendBufferSize is set to 51200 bytes. At the end of the method ,a Ping is called with a random number of milliseconds from 10000 to 15000.
The static object Info method is used to retrieve victim computer details, such as ID, Username, OS Full Name and other OS details.
The method INDATE saves the current datetime of the last file write operation on the Helper.current object, the method Spread performs settings to permit the infection through USB devices.
The method UAC tries to perform Administrator rights checks:
Here we have the static string method Antivirus(), it is used to get details and information of currently installed Antivirus products on the victim machine.
The GPU and CPU details are also obtained:
XClient gets information about the installed RAM memory:
The BeginReceive method gathers the buffer of data read from the sockets and C&C communications, if the EndReceive method result is greater than zero, the lenght of the buffer is checked, if it is empty and the first cell of the Buffer object is zero it starts the receiving handler, instead the WriteBuffer method is called with the first cell of the Buffer object.
The BeginRead calls the Messages.Read method with the byte array b as argument. The static void method Send gets as argument a string object called msg, the message is encrypted in AES algorithm and then it is sent with sockets through MemoryStream objects.
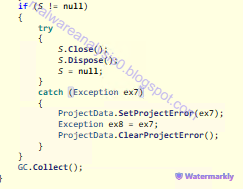
Here we can see the closing event of the communication and C&C connections and the dispose of the objects used.
The Pong and Ping methods are used respectively to increment Interval value while the connection is up, the Ping method sends ping commands to maintain a keep-alive communication.
The internal class Helper contains variables and object used in previously mentioned methods, such as used useragents, mutexes and current process filename.
Here we have details related to domain names and host names validation checking, input time.
XWorm threat has a prevention method for thread sleep status by changing execution state of threads:
The method GetHashT is used to hash in MD5 the bytes buffer taken in input. The method SetValue performs registry key settings in CURRENT_USER key.
The method Decompress uses GZip function to decompress the byte array “input” taken in input:
The compress method compresses with GZip algorithm the “input” bytes array taken as argument.
Here we have the two methods of type byte[] that perform AES encryption and decryption of the bytes array taken as argument:
The method CreateMutex could create a new mutex object:
The Main method performs the initial AES decryption of the main attributes for the infection and C&C communications, such as Hosts, Port, KEY (AES Encryption key), SPL, Groub (threat version) and USBNM.
The Messages class is used to perform operations based on commands received, the commands are evaluated with a switch construct in the try-catch structure, for example uninstall command operation.
Here are the details of the switch construct related to the DDoS operations, which include DDos.Start which takes the input argument with the first cell of the array used to perform massive operations and the DDos.Abort function to stop the DDos operations.
The command “Hosts” permits to perform hosts file modification and file read to perform DNS poisoning.
The static void method Plugin takes as argument a byte array called B and sets hardcoded needed attributes for Invoke operations. The parts of the Pack object are encoded in Base64.
The static void SendMSG method performs the sending operation through the ClientSocket object of the messages objects.
The method TD takes the Input argument of type string, it creates a thread to perform POST requests with a custom useragent, got with a random getting operation in the Helper.userAgents array with Content-Length size of 5235 bytes. There is a sleep of 2.5 seconds of the thread and then the socket is disposed.
The Monitoring method takes an argument called Data of object type string, the SendMSG method is called with “Open” messages and process window titles. The OpenUrl method performs requests through HTTPWebRequest objects and it calls a Process.Start instance with the URL in question.
The boolean Cam method checks the driver information:
The method RunDisk checks the extension of the file related to obj object, if the extension is related to the PowerShell scripts .ps1 then the scripts are run:
The static object Memory method takes as argument the bytes array buffer, it is loaded in an Assembly object, the entrypoint is taken and then the assembly object is invoked with specific parameters, this could be used also in the compilation of dropped multi-stage artifacts.
The Uninstaller method is used to lunch a bat CMD script to remove the XWorm threat and all the leftovers.
With a network dynamic analysis we can see malicious ping in loop to the malicious C&C IP address 147.124.210[.]158.
The IP address 147.124.210[.]158 is recognized as malicious by OSINT sources, it has been registered by Majestic Hosting Solutions, LLC in United States of America.
The IP address in question has the open port 3389 and the RDP service, used for malicious remote access:
The JARM thumbprint 2ad2ad16d2ad2ad22c2ad2ad2ad2adfd9c9d14e4f4f67f94f0359f8b28f532 is related to other malicious IP addresses, involved in malicious and suspicious remote access activities.
IOCs:
e22d80df02163d375fa6a7b08700eb01
05fbdaaad1ffbee891739f8a0df2cae8059d4011
0dae41b10dc8aac507b9634de862384ee712c230f3ed1fed2075e5884ad75972
Raw[.]githubusercontent[.]com/rosarioian181/meeekone
147.124.210[.]158
f2ce039294ad313d2a9a84855c27341d
bbb87057a6b476ac988766dd14dc73b7a802b472
e328af9decf08bcaab7ada74100cc56186383a3bf51c9de6a9d7b41ea3aea094
XClient.exe
Customer.exe
Customer.ps1
RuntimeBroker.exe (in AppData\Local\Temp)
2ad2ad16d2ad2ad22c2ad2ad2ad2adfd9c9d14e4f4f67f94f0359f8b28f532
YARA rule:
rule XWormRule_December_2024
{
strings:
$str = "Temp/RuntimeBroker.exe"
$hex = { 54 65 6d 70 2f 52 75 6e 74 69 6d 65 42 72 6f 6b 65 72 2e 65 78 65 }
condition:
$str or $hex
}
CONCLUSION:
This sample of XWorm threat reveals some differences from others variants (not only newer), such as the adding but also removing of some malware modules, for example DDos, ransomware module. As another difference from the version 3.1 the main artifact has been developed in .NET and not in C++. Another difference is Crytocurrencies stealing specific module. This type of threat, also thanks to its wide distribution in Darknet forums and its opening to MaaS structure and approach, could be more and more invasive, dangerous in its characteristics and main malicious activities but also evading capabilities. For example, in the future threat landscape it could not be so difficult to see effectively a new XWorm variant obfuscated heavily, with more modern malicious features, such as a wiper with new characteristics like file extensions appending (similarly to BiBi Wiper), used in geopolitical conflicts, new exploitation techniques used in the infection cycle (for example in the DoS context the targeted usage of the exploitation of the vulnerability CVE-2024-3393 in Palo Alto firewalls approach) and stages, fileless malware infection techniques without specific artifacts dropping.
Sources of the OSINT screenshots: Virustotal, Censys, AbuseIPDB